What Is a Hash in Blockchain?
Content
Hashing, the bedrock of blockchain technology, is a complex concept with profound implications for bolstering digital security and upholding data integrity across the network.
The hash function assumes a pivotal role in the realm of blockchain technology, serving as the underpinning for cryptocurrencies’ operations. Furthermore, hashing transcends mere data encryption, serving as an integral component within cryptographic processes like Proof-of-Work (PoW), that is, the mechanism essential for validating and appending new blocks to the blockchain. This fortifies security and guarantees transparency, verifiability, and the immutability of the decentralized data ledger.
Within the confines of this article, we shall delve deeper into the role of hashing and its fundamental attributes, and rudimentary cryptographic hash functions and elucidate why the significance of hashing lies in its capacity to cultivate trust within a “trustless” environment.
What is a Hash Function?
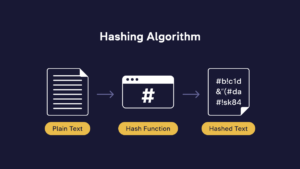
A hashing function is a mathematical algorithm that converts an input signal into a fixed-size string, typically a hash value. This deterministic transformation means a specific input consistently produces the same hash output. Simultaneously, it possesses a one-way characteristic, preventing the retrieval of the original input signal from the hash value.
Hashing emerged in the early days of computer science, primarily for streamlining data retrieval processes. As time passed, its applications grew considerably, particularly within cryptography, and evolved into a pivotal element for safeguarding data integrity and security in today’s digital landscape.
Hashing algorithm
How does hashing work? Imagine you possess a legal contract, a multipage document outlining an agreement between two parties. You employ a hash function, such as SHA-256, on this document. This function processes the entire contract’s text regardless of length or complexity, producing a unique string of fixed-length characters. For instance, this hash might resemble something like this: 3f786850e387550fdab836ed7e6dc881de23001b.
Rather than uploading the complete text of the contract into the blockchain, only the hash gets stored within it — something like 3f786850e387550fdab836ed7e6dc881de23001b. This approach conserves space and enhances privacy. It becomes immutable once a hash value is “embedded” within a block and integrated into the blockchain. In other words, altering even a single character in the original contract will result in an entirely different hash.
Subsequently, if a need to verify the contract’s authenticity arises, the same hash function is applied to the present version of the document. The resulting new hash is then compared to the one stored in the blockchain. If the hashes align, it confirms that the contract hasn’t undergone any alterations since it was hashed and preserved.
In this manner, hashing not only condenses the data, making it more efficient for storage, but also ensures the document’s integrity since any modification to the document produces a hash distinct from the original. Moreover, by exclusively storing the hash, the contract’s actual content remains confidential and outside the blockchain’s purview.
How Does Hashing Work in Crypto?
How hashes work in crypto? Let’s explain the hashing process using the example of the Bitcoin network.
Bitcoin uses the SHA-256 algorithm (Secure Hash Algorithm 256-bit).
Block Header
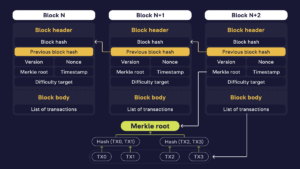
Each new block contains a Header and a Body, which includes a List of Transactions and other service information.
The Block Header is a crucial element, comprising a structured collection of data that miners “manipulate” to discover the accurate hash for a new block. Now, let’s delve deeper into the information contained within the block header in the Bitcoin network:
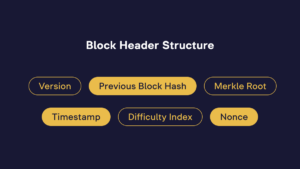
- Version is a 4-byte number indicating the current block version.
- Previous Block Hash is a 32-byte hash of the last block in the chain. This is a critically important aspect of blockchain security, as it creates a continuous interlinked chain where each block is cryptographically tied to its predecessor.
- Merkle Root is a 32-byte hash representing the root of the Merkle tree.
- A timestamp is a 4-byte number reflecting the time of creating a new block.
- Target Difficulty (or Difficulty Index) is a 4-byte number that defines the difficulty conditions. The network regulates it and aims to create a new block approximately every 10 minutes.
- Nonce is a 4-byte number selected by miners. They frequently change the Nonce and recalculate hash values to find one that meets the difficulty criteria.
Creating a new block involves combining these elements with a random number (Nonce) and applying a blockchain hashing algorithm (such as SHA-256) to this formula.
Version
+
Previous Block Hash
+
Merkle Root
+
Timestamp
+
Target Difficulty
+
Nonce
↓
Hashing (eg with SHA-256)
=
Hash
In this process, miners strive to find a hash for the new block that matches the current network’s difficulty level. To do this, they need to repeatedly change the value of Nonce and recalculate the hash value until they find one that meets the specified criteria. The result is a unique hash representing the entire block.
The Hash Rate is the total computational power of the network, or the number of hashes computed by a mining device per second. This metric reflects the efficiency and productivity of mining devices and is measured in hashes per second (H/s).
This metric is a crucial indicator of the network’s “strength.” It is also measured in units such as kilohashes per second (KH/s), megahashes per second (MH/s), gigahashes per second (GH/s), terahashes per second (TH/s), and so on, increasing as computational power grows. In the case of Bitcoin, it’s measured in EH/s (exahashes per second).
The “body” of a block stores all the transactions that will be included in it. Interestingly, despite the theoretical upper limit on the block size historically set at 1 MB, the actual size of a block in terms of the number of transactions can vary. A block would, previously, store anywhere from 2000 to 2500 transactions, considering their average size. However, with the Taproot upgrade, this limit has only increased. Transaction data has become more compact, allowing for more efficient utilization of the available block space.
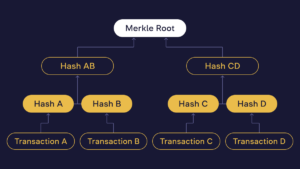
A method known as the Merkle Tree algorithm is used to process all the transactions in a block, and hashing is also applied in this process.
Merkle Tree
Each transaction within a block undergoes a two-step hashing process. Initially, each transaction is individually hashed. Subsequently, these transaction hashes are combined and hashed together. This process involves using a cryptographic hash function to transform the transaction data into a fixed-size hash. Then, individual transaction hashes are paired and hashed again. If the number of transactions is odd, the last hash is duplicated and hashed with itself to create an even number of hashes. This process continues until only one hash remains—the root or the Merkle Root, as it is known.
The Merkle Root is a unique representation of all the transactions in a block and is included in the block’s header. The Merkle Tree enables efficient and secure verification of the contents of each transaction in the block including transaction IDs, ensuring their integrity. Any alteration in a single transaction would change the Merkle Root value and the hash of the entire block. Modifying one block becomes computationally impractical since it necessitates rehashing every subsequent block. This cascade effect makes altering data in the blockchain exceptionally challenging and resource-intensive.
As a result, hashing in blockchain technology ensures the integrity and security of crypto transactions, making the blockchain a reliable and tamper-resistant ledger — a crucial aspect in a system where trust and security are paramount.
The Purpose and Role of Hashing in Cryptocurrencies
Based on the information provided earlier, it becomes clear that the blockchain operates as a decentralized ledger composed of cryptographically connected blocks. Hashing is a pivotal mechanism that forms the foundation for both the security and operation of this technology.
To sum up, the hashing algorithm plays a critical role in multiple essential processes:
- Transaction Hashing + Merkle Tree: All transactions are grouped into a block. Each individual transaction undergoes hashing. Then, they are paired together and hashed again. This process is repeated recursively, and hashes are combined until only one hash remains for all transactions in the block — the Merkle Root. This Merkle Root serves as a unique representation of all transactions in the block and is included in the header.
- Block hashing: After a block is filled with transactions and its Merkle Root is calculated, the entire block header and its content undergoes hashing. Miners attempt to compute this final hash during the cryptocurrency mining process.
- Mining (in the context of PoW): In the mining process, miners compete to find a specific hash that meets certain criteria set by the network’s difficulty level. This involves repeatedly hashing the block header with different Nonce values until they find a hash that satisfies the specified criteria. The first miner to achieve this adds a new block to the blockchain.
- Blockchain integrity: Each new block in the blockchain contains the previous block’s hash. This creates a chain of blocks and ensures the integrity of the blockchain. Any alteration to a transaction changes the hash of the block containing the transaction and affects all subsequent blocks.
- Network security: When a miner successfully mines a new block (finds the correct hash that meets the network’s difficulty criteria), the block is broadcast to the network and relayed to nodes. Nodes verify the validity of the new block using hashing.
These checks are necessary to ensure that the block complies with network rules and contains only valid transactions (i.e., they verify that they are correctly formatted, and signed, and there is no double spending). And if the block passes all these checks, nodes accept it and add it to their copy of the blockchain. Then, this consensus is gradually transmitted to other nodes, reaching consensus across the entire network.
Features of Blockchain Hash Function
From a technical standpoint, a cryptographic hash function must adhere to several fundamental properties to be considered secure:
- Fixed-length output for any input:
To understand how this works, let’s take the text blockchain hash example:
The creation of the WB network was implemented as part of developing the WhiteBIT Token (WBT), the exchange’s native asset. Thanks to the successful implementation of the WB Network blockchain, WBT found a new home, becoming the full-fledged WBT Coin (WBT) cryptocurrency.
We use the SHA-256 algorithm and get: 8b91d751f2773738c1b38e9ad25440aca3e99d59947345ec47bb04e5d9ce6493. The length of the text can vary, but the length of the hash will always be fixed.
- Deterministic: The same message should always result in the same hash code. Look again at the hashing example above. Anyone applying the SHA-256 function to the exact text will get the same hash. This property enables all participants to reach a consensus.
- Collision resistance: It is practically impossible to find two sets of data that produce the same hash.
In other words, in a fundamental sense, the original data, for example, “Hello, WhiteBIT!” and “Hello, World!” will not have the same hash values. The probability of obtaining the same hash from identical input data should be close to zero. Collision resistance is crucial for ensuring data integrity and non-repudiation.
- Pre-image resistance: This is the ability of a hash function not to reveal any information about the input data. This property is crucial for ensuring the security and integrity of cryptographic systems, including those used in blockchain technology.
Common hashing algorithms in blockchain
Several crypto-hashing algorithms are commonly employed in the blockchain space, each with unique properties and capabilities. The most well-known ones include:
- SHA-256 (Secure Hash Algorithm 256-bit) is used in Bitcoin (BTC), Bitcoin Cash (BHC), and various Bitcoin forks.
- KECCAK (SHA-3) is utilized in newer and less widespread blockchain implementations, representing one of the latest additions to the family of secure hashing algorithms.
- Ethash was formerly used in Ethereum (ETH) before transitioning to Proof-Of-Stake (PoS).
- Scrypt is employed in Litecoin (LTC), Dogecoin (DOGE), and various other altcoins.
- X11 is put to use in Dash (DASH).
The Bottom Line
As we’ve discovered today, hashing isn’t just a mathematical tool. It’s an indispensable element of the modern digital landscape, particularly regarding enhancing security and integrity. Its applications extend beyond simple calculations, playing a crucial role in cybersecurity, data verification, and blockchain technology. Hashing functions provide robust protection for confidential information, ensure digital data’s authenticity, and bolster decentralized systems’ resilience. This multifaceted utility of hashing underscores its significance beyond traditional mathematical applications, making it a pivotal component of contemporary technological infrastructures.
FAQ
A hash is a unique string of characters with a fixed size created using a specific hashing algorithm applied to input data.
It helps secure blockchain technology by ensuring the integrity and security of data, transforming each transaction and information stored in a block into a unique fixed-size hash. Any alteration of data in a transaction results in a different hash, making tampering evident. As a result, an immutable record of transactions is created because changing any block would require rehashing the entire chain, which is computationally infeasible.
One of the primary purposes of using a hash function is to ensure data integrity. It processes data to generate a unique fixed-length hash value, acting as a “digital fingerprint” of the data. Any alteration to the input data, no matter how small, results in an entirely different hash, making it easy to detect unauthorized changes. This property of hash functions is crucial in various systems, including; transaction security, verifying data integrity, and maintaining data consistency in structures like blockchain.